How does Azure AD protect my organisation?

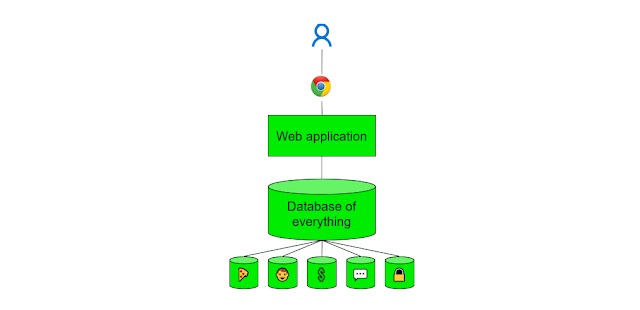
I'll assume you've read my first post, which is a gentle introduction to modern authentication . We now look at some of the security advantages of using Microsoft's Azure AD to act as your Identity Provider. Azure Active Directory ('AAD') is of course the cloud successor to the very successful Active Directory, a distributed directory of users introduced at around the turn of the century. Active Directory used a protocol called Kerberos (developed outside of Microsoft in the 80s and 90s) to carry out that all-important authentication handshake and carry tokens around the system. The Azure version uses OpenID Connect, a widely used authentication protocol built on OAuth 2.0. This ensures that the user's user name and password are not seen by the relying application, and that only the relying application can read and trust the token from AAD. Connect your applications As a company, you configure or write your applications to connect to AAD for authentication, and