Going deeper with AAD B2C
AAD B2C custom policies are a key feature that allows you to customize the authentication process according to your specific requirements.
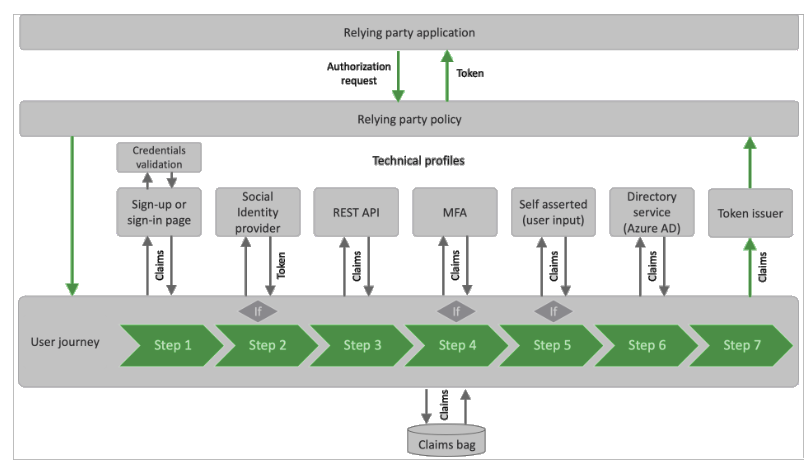
Technical Profiles are an integral part of AAD B2C custom policies. They define the technical details of an identity provider, such as an external identity provider or a local account, and how it should be used in a user journey. Technical profiles can also define the data that is collected from the user and passed to the application. In custom policies, technical profiles can be used to define the steps that are performed during a user journey, such as logging in, registering, or resetting a password.
User Journey steps are the steps that are performed during an authentication or authorization process. AAD B2C custom policies allow organizations to define the user journey steps that are performed during an authentication or authorization process, such as logging in, registering, or resetting a password. These steps can be defined using technical profiles and can include collecting user data, verifying the user’s identity, and granting access to the application. User journey steps can also include calling external REST APIs to retrieve information or perform other actions.
One of the key capabilities of AAD B2C custom policies is the ability to call external REST APIs. This enables organizations to integrate with external systems, such as databases or customer relationship management (CRM) systems, to retrieve information or perform actions during a user journey. For example, during the registration process, an API call can be made to retrieve information about the user from a CRM system, or during the login process, an API call can be made to verify the user’s identity in an external identity provider.
AAD B2C custom policies provide organizations with a powerful tool for managing access to their applications and services. The use of technical profiles and user journey steps, along with the ability to call external REST APIs, enable organizations to customize their authentication and authorization processes to meet their specific requirements. By using AAD B2C custom policies, organizations can ensure that their authentication and authorization processes are secure, efficient, and meet their specific business needs.



Comments
Post a Comment